Detect advanced attacks and correlate abnormal behavior with scheduled searches and alerts
In the latest version of Panther, you can detect advanced attacks like C2 beacons, unusual login attempts, password spraying, and more by scheduling searches and alerts against your security data lake.
With Panther’s new Scheduled Queries feature, you can analyze all of your collected log data to bring more context and correlation to your threat detection efforts. By scheduling searches to run on intervals against your data lake, user and machine behavior can be evaluated across applications and systems to identify malicious activity that would otherwise be difficult to detect.
Scheduled Queries add a powerful new threat detection model to Panther’s existing real-time detection engine. By giving security teams the ability to retrospectively analyze and alert upon all of their log data, Scheduled Queries help organizations identify activity like C2 Beacons, Unusual Logins, Password Spraying, DNS Tunnels, and even perform operational reporting like building summaries about the state of cloud infrastructure compliance.
Scheduled Queries are simply SQL queries that are set to run against your collected log data on a predefined schedule. When scheduling the query, you have the option of using a crontab or a simpler period-based frequency. If using a simple period, you can enter the number of days and/or minutes after which the SQL query should run again. For example, setting a period of 0 days and 30 minutes will result in a query running every day, every 30 minutes (give or take a few seconds).
The output of the query are passed through Panther’s rules engine for potentially further analysis by a “Scheduled Rule.” In the Scheduled Rule, you can define and configure all of the alert-related settings your team needs to create high-fidelity alerts, such as title, deduplication period, thresholds, and more.
In its simplest form, a Scheduled Rule can simply return True to trigger an alert each time the query runs and an output is generated. But as desired, Scheduled Rules can be used to perform additional post-processing analysis of the query to further filter results and identify malicious activity.
To better understand how Scheduled Queries and Rules are used for threat detection, let’s start with a simple end-to-end scenario.
Assume your organization very carefully restricts access to the AWS console from a specific set of known IP addresses, and you want to get alerted any time there’s a login from outside this IP space. To verify this security control is working as expected, you can schedule a query to check and confirm that all AWS console logins have a sourceIPAddress from within this IP space.
To get a running summary of the IP addresses associated with user logins, we can schedule the following SQL query to run every 15 minutes, checking the previous 30 minutes of activity:
SELECT
ct.*
FROM
panther_logs.public.aws_cloudtrail ct LEFT OUTER JOIN infrastructure.networking.egress_blocks egress
ON (ct.sourceIPAddress = egress.ip)
WHERE
p_occurs_since('30 minutes')
AND
ct.eventtype = 'AwsConsoleSignIn'
AND
egress.ip IS NULL -- NOT matching!
LIMIT 1000 -- we don't expect many of these BUT we have this here for safety!Code language: SQL (Structured Query Language) (sql)Now in the Panther UI, we’ll save this query and set a schedule for it to run every 30 minutes:
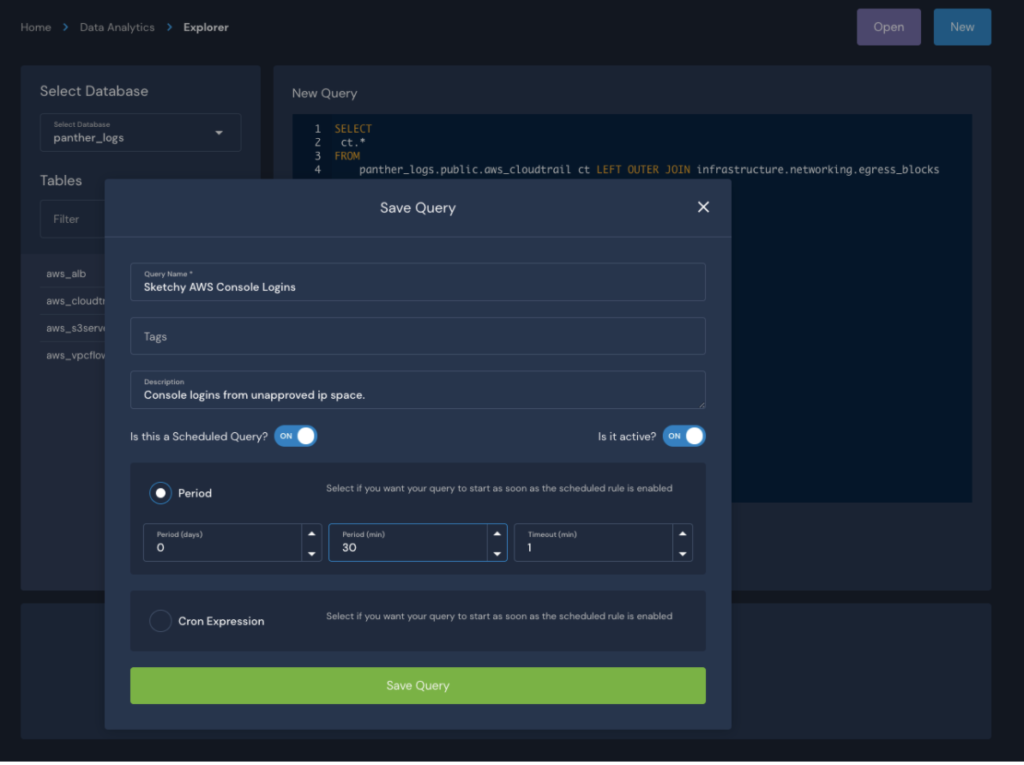
Once the Scheduled Query is running, we’ll navigate to our Detections interface and create a Scheduled Rule that targets the output of our Scheduled Query:
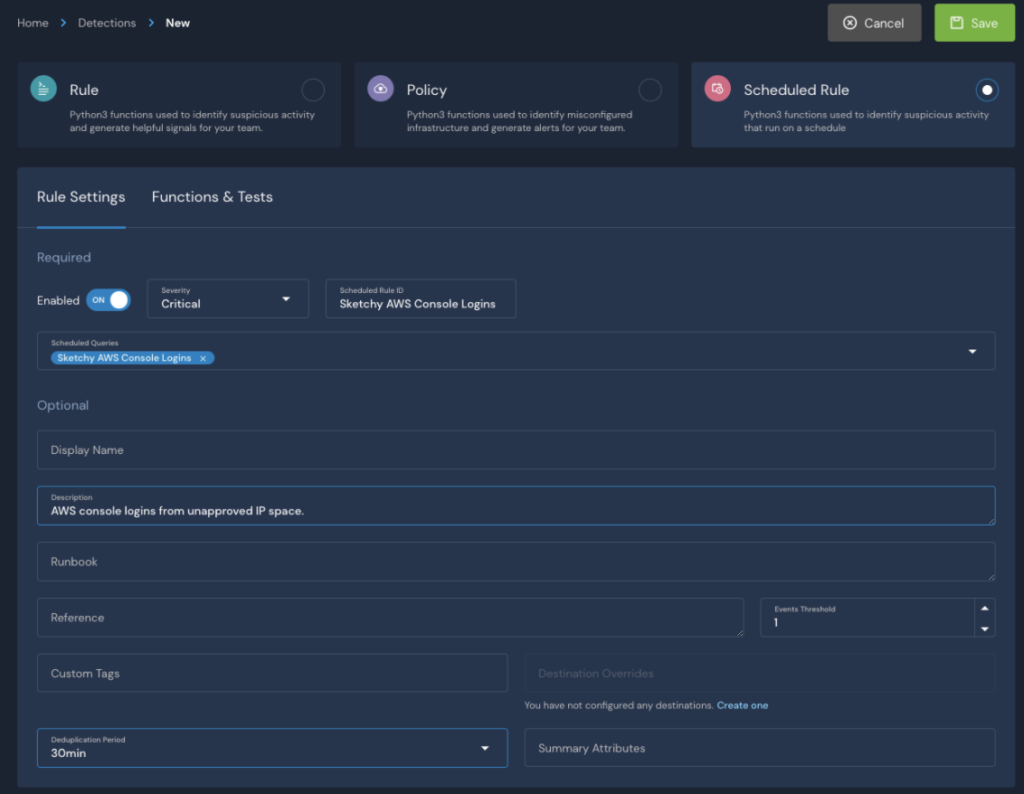
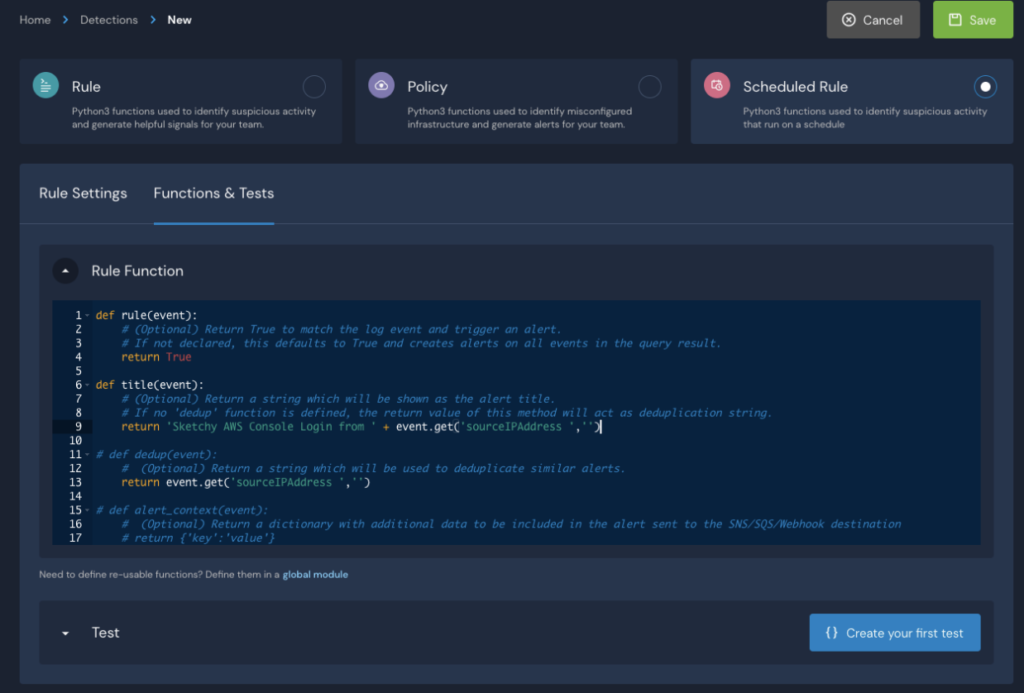
As mentioned previously, in the Scheduled Rule, you can customize the alerts and define destinations. In addition, to avoid alert storms, in the above Scheduled Rule we use the sourceIPAddress to deduplicate events and set the deduplication window to 30 minutes.
Now, any time a user accesses the AWS Console from outside of our known IP block, the security team will get an alert!
In this blog, we explained what Scheduled Queries are, and how you can start using them to detect threats and secure your organization. To learn more about Scheduled Queries, read the documentation and review our example queries.
Panther ships with pre-built integrations to quickly set up security monitoring for a number of popular security and productivity applications your organization likely uses today. Request a demo to learn how Panther can help you build a world-class detection and response program.
