Here’s how you can use Panther to detect and investigate malware, like Sunburst:
Breaches like Sunburst, that is impacting Solarwinds, a network management software company, go far beyond the company. In this case, the malicious code is projected to have impacted nearly 18,000 customers in a supply-chain compromise.
FireEye believes that attackers trojanized SolarWinds Orion business software and distributed malicious but legitimately signed updates to its customers. This resulted in a widespread compromise, lateral movement from within victim environments, callbacks to C2, and potential exfiltration of sensitive data. The Backdoor.Sunburst attackers also used multiple obfuscated blocklists to identify security tools and processes, which left multiple backdoors, so they could keep a presence in the network for later stages of an attack.
Today, Panther has published an addition to our open source detections to actively track malware callbacks to the Sunburst Indicators of Compromise (IoCs) as identified by FireEye. These can be easily uploaded to your Panther deployment to immediately analyze your critical log data, like VPC Flow logs, Cisco Umbrella, and more. In this blog post, we’ll outline how these detections work and give you a formula for tracking any type of IoC list.
For more details about the associated IoCs, network activity, and what we used as a reference to write our detections, read FireEye’s in-depth blog post. Also, for the full list of IoCs and detection signatures, check-out FireEye’s countermeasures.
With Panther’s Python modules, you can define detection logic and datasets in one place, like threat intelligence, that can be used across multiple detections.
In this case, the Sunburst IOCs gathered from FireEye’s report are added into a new global module called panther_iocs, which is then used by our detections to analyze incoming logs for the identified known indicators.
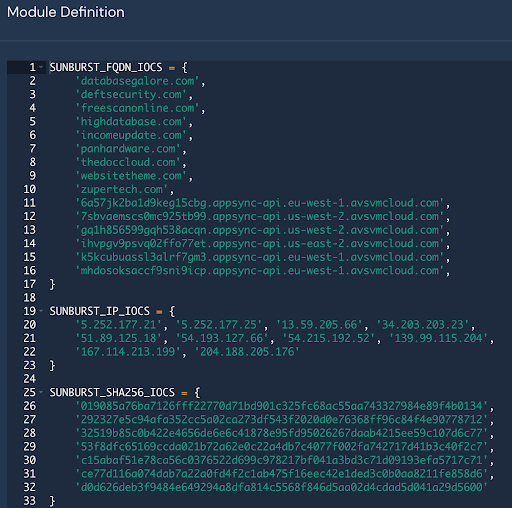
The Python rule below imports the IOC module and will identify hits on indicators by utilizing the Panther standard fields, in this case, p_any_ip_addresses. During the data normalization process, these “standard fields” are populated to pull atomic indicators into the top-level that can otherwise be difficult to access. Standard fields also enable threat-hunting by creating a rich metadata layer across all of your critical security data:
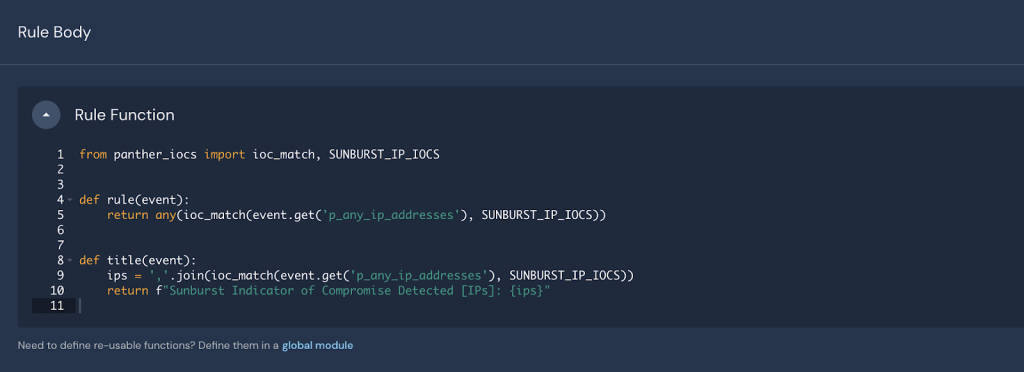
In addition, because indicator fields are consistent across all logs, simple rules like the one above can be applied to many different environments. For example, this rule is applied to logs from Okta, AWS, Cisco Umbrella, and more.
Now, if any of the IPs from our threat intelligence data appear within new logs from these systems, security teams will receive a high-value alert to investigate.
Finally, to determine if these indicators ever previously appeared in your systems, Panther’s Indicator Search can be used to find hits across all of the collected logs in the security data lake:
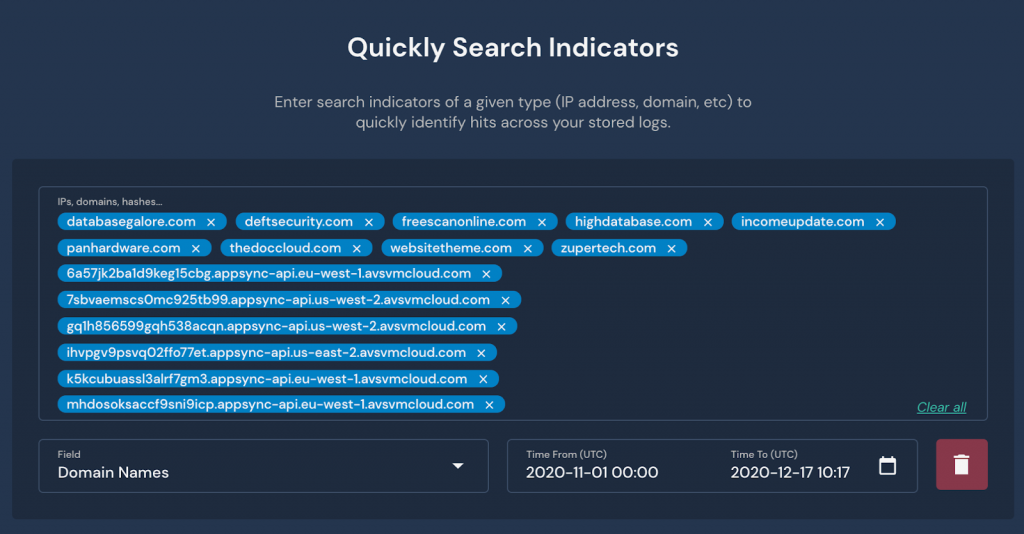
The search displays a timeline of all hits, grouped across logs and previously generated alerts in the specified timeframe.
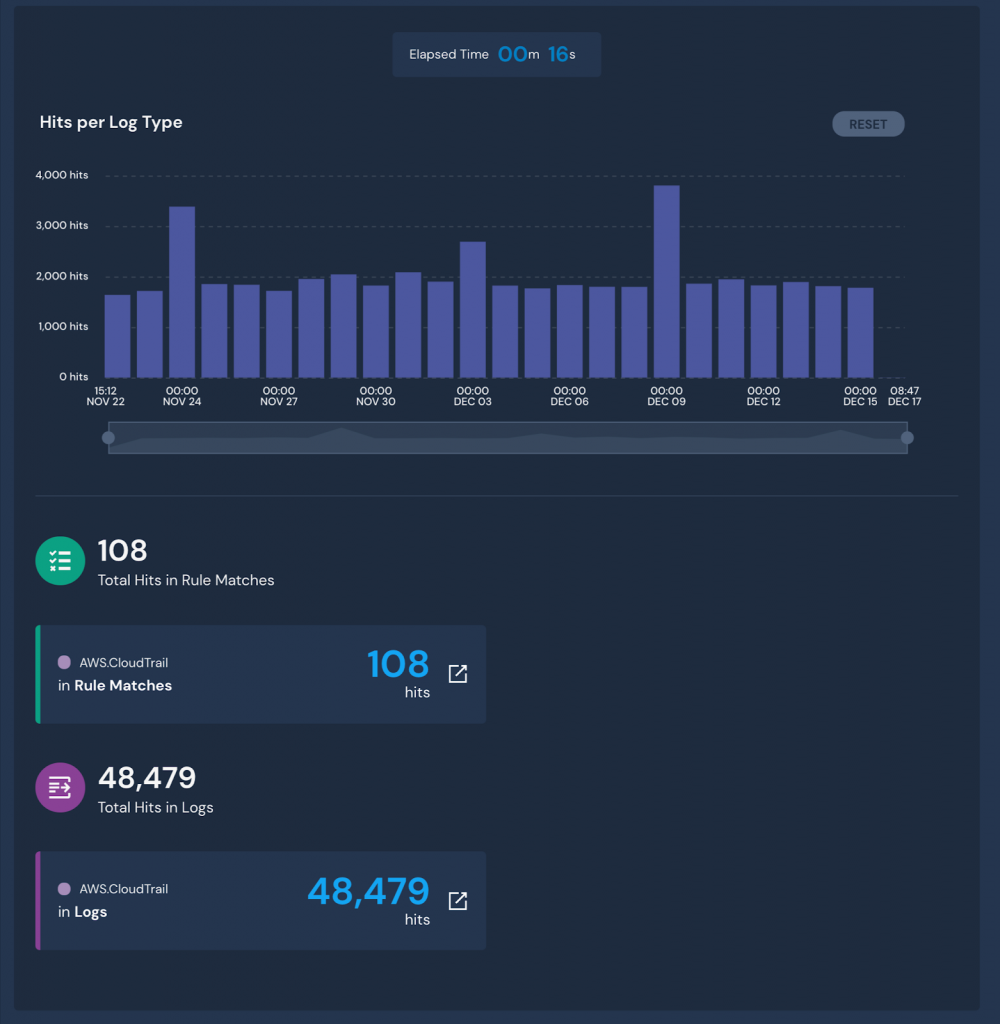
To further investigate, pivot directly to the hits with Panther’s data explorer and continue to refine your analytics using SQL:
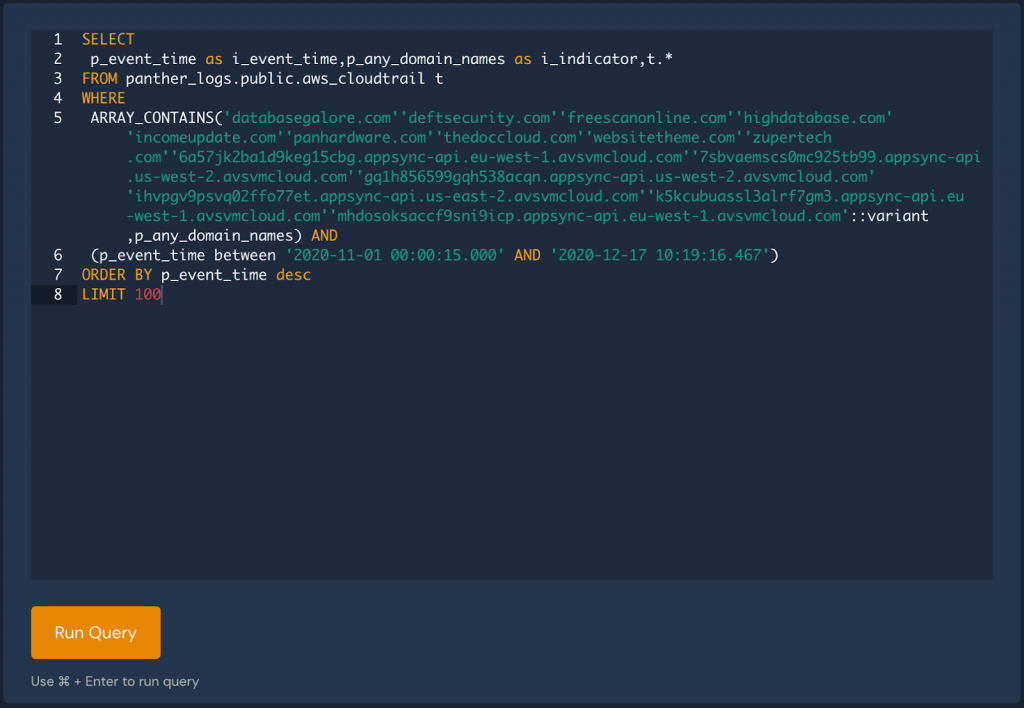
Results can be shared with your team to identify root cause, impacted systems, and tell the full story.
Detecting a sophisticated breach starts with a clear understanding of what’s happening across your environment. This sounds simple, but requires that all logs are continually collected and retained in a searchable format, at a high scale. Panther takes care of all of the heavy lifting, data transformation, detection, and alerting, built fully on top of a scalable data lake with Python and SQL as the tools to improve your monitoring posture.
Get started by downloading our newest detections and uploading them to your instance of Panther:
https://github.com/panther-labs/panther-analysis/releases/tag/v1.14.0 (zip)
Thanks and Happy Hunting!
